How Dome Works
Dome interposes between users and your agent, inspecting traffic in both directions:Accessing Guardrails
Navigate to Guardrails in the sidebar to view all registered agents and their protection status.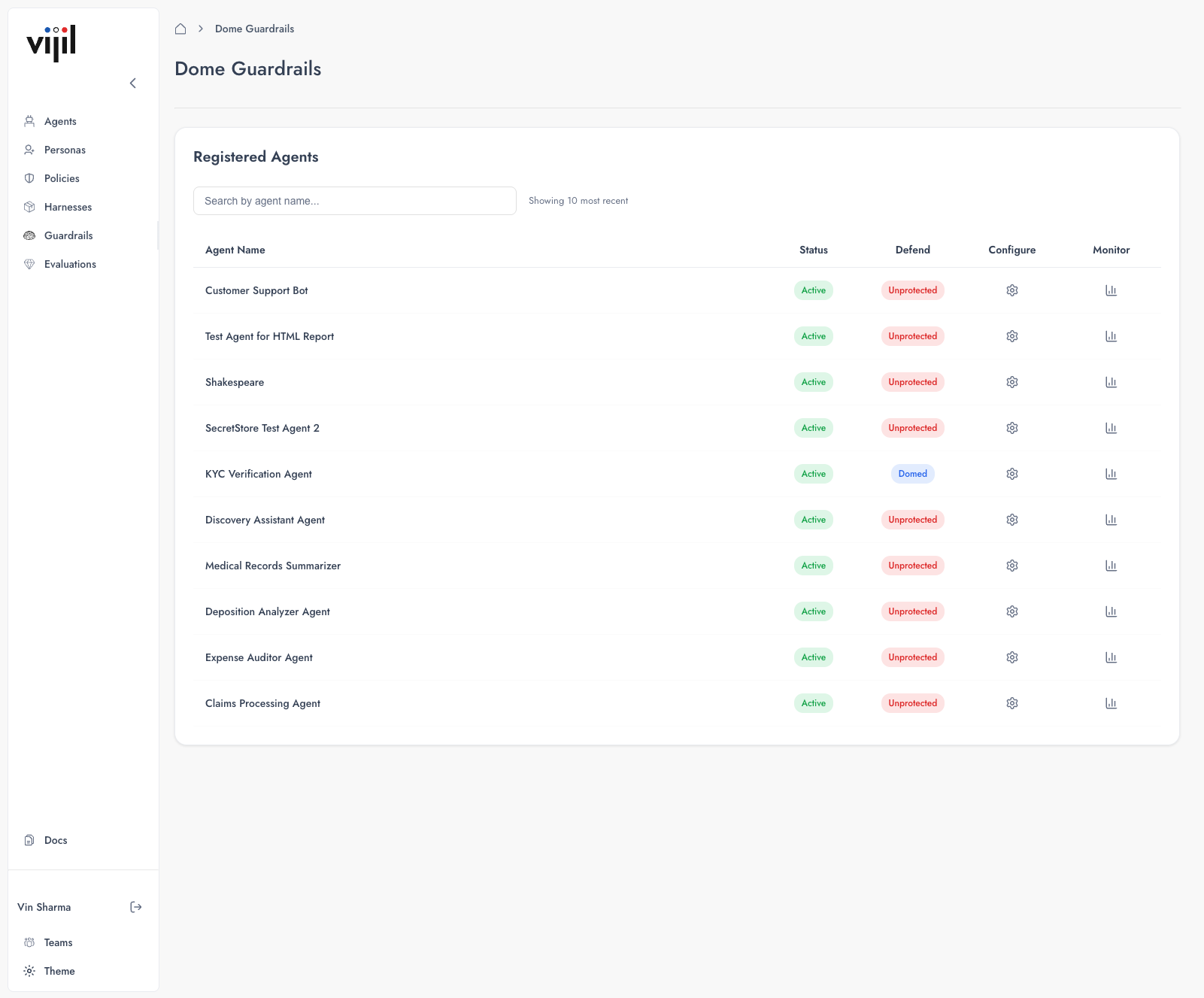
| Column | What It Shows |
|---|---|
| Agent Name | Identifier from registration |
| Status | Active or Draft |
| Defend | Protection status: Unprotected or Domed |
| Configure | Access guardrail configuration |
| Monitor | View observability dashboard |
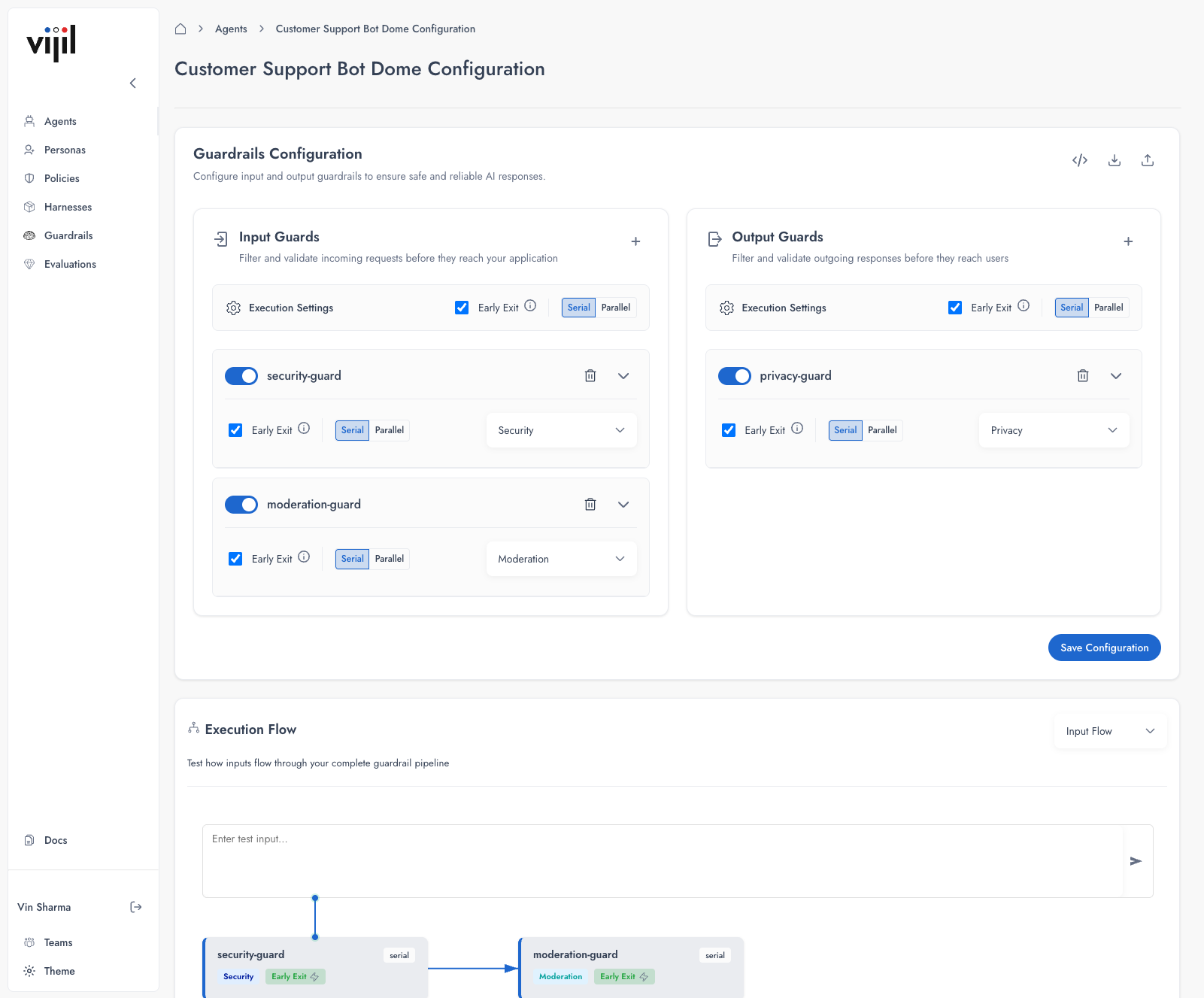
Adding Guards
Click the + button in either the Input Guards or Output Guards section to add a new guard.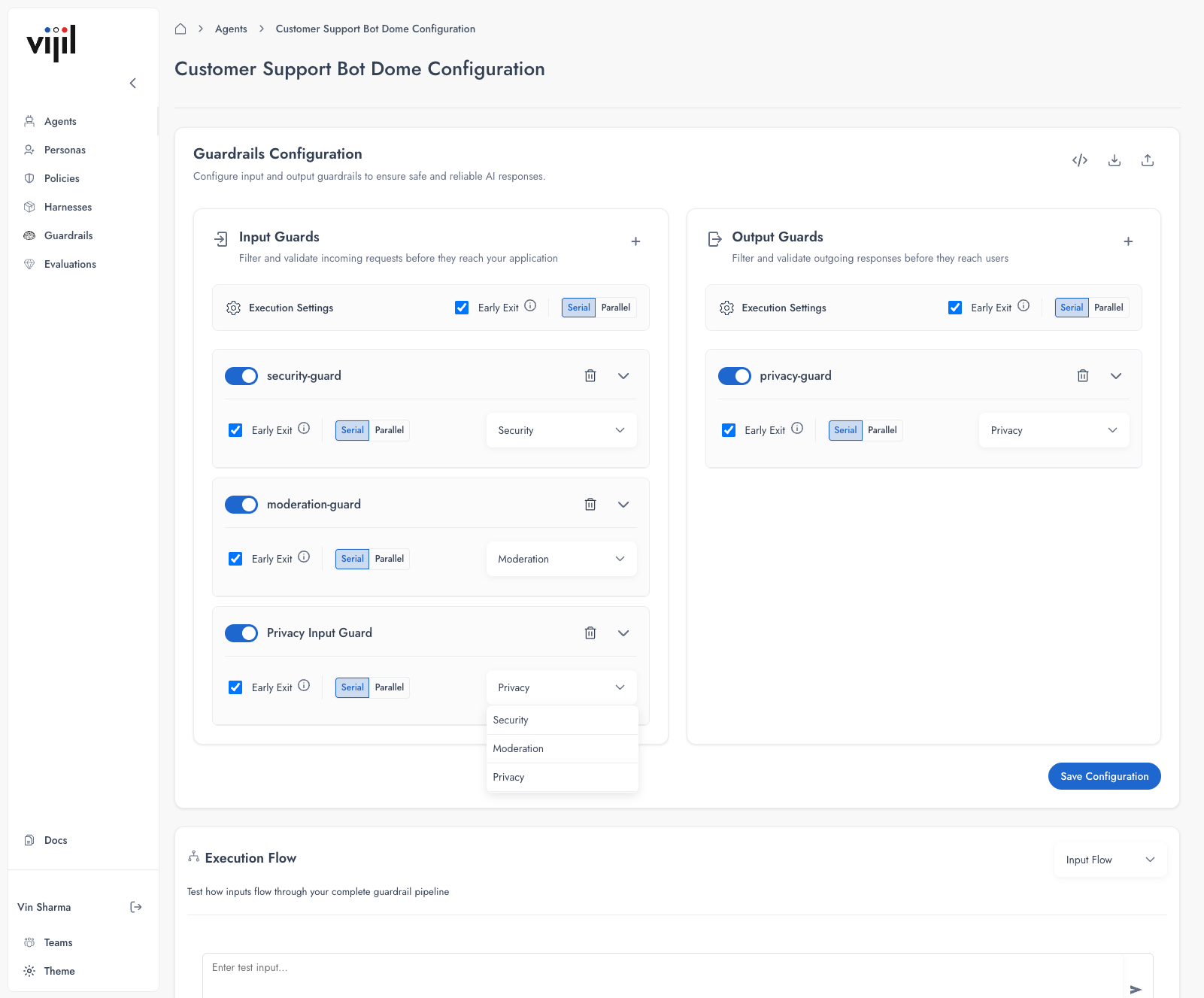
- Security — Detect adversarial inputs
- Moderation — Filter harmful content
- Privacy — Protect sensitive data
Security Guards
Security guards protect against adversarial inputs designed to manipulate your agent.| Threat | Description |
|---|---|
| Prompt Injection | Attempts to override system instructions |
| Jailbreak | Attempts to bypass safety guidelines |
| Encoded Attacks | Malicious content hidden in encodings (Base64, Unicode) |
| Adversarial Suffixes | Appended strings that trigger unsafe behavior |
encoding-heuristics— Detects encoded content that may hide malicious payloadsprompt-injection-mbert— ML model trained to identify injection attempts
Moderation Guards
Moderation guards filter content that violates usage policies or community standards.| Category | Examples |
|---|---|
| Toxicity | Hate speech, harassment, threats |
| Violence | Graphic violence, incitement |
| Sexual Content | Explicit or inappropriate material |
| Self-Harm | Content promoting self-injury |
moderation-flashtext— Fast keyword-based detectionmoderation-deberta— ML model for nuanced content classification
Privacy Guards
Privacy guards detect and protect personally identifiable information (PII).| PII Type | Examples |
|---|---|
| Email Addresses | user@example.com |
| Phone Numbers | +1-555-123-4567 |
| SSN / Credit Cards | 123-45-6789, 4111-1111-1111-1111 |
| Addresses / Names | Physical addresses, personal names |
privacy-presidio— Microsoft Presidio-based entity recognition
Execution Settings
Each guard has configurable execution settings.Early Exit
When enabled, processing stops if this guard flags the input. The request is blocked without executing subsequent guards.- Enable when a detection should definitively block the request
- Disable when you need comprehensive logging of all detections
Execution Mode
Serial — Guards execute in sequence. Use when guard order matters or later guards depend on earlier transformations. Parallel — Guards execute simultaneously. Use when guards are independent and you want lower latency.Guard Pipeline
The order of guards determines the execution pipeline. Use the Execution Flow panel to visualize how requests flow through your guards.Input Guard Pipeline
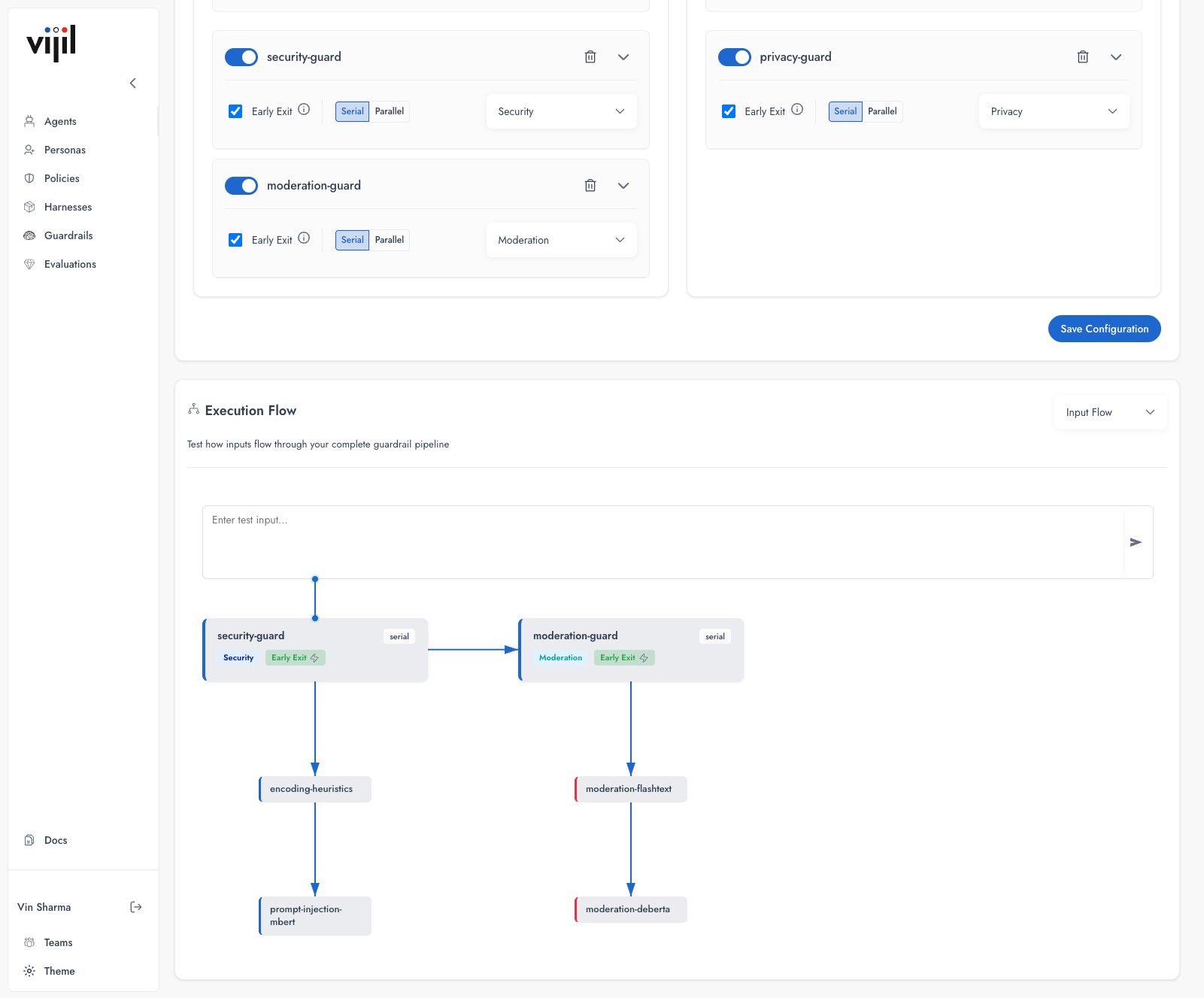
Output Guard Pipeline
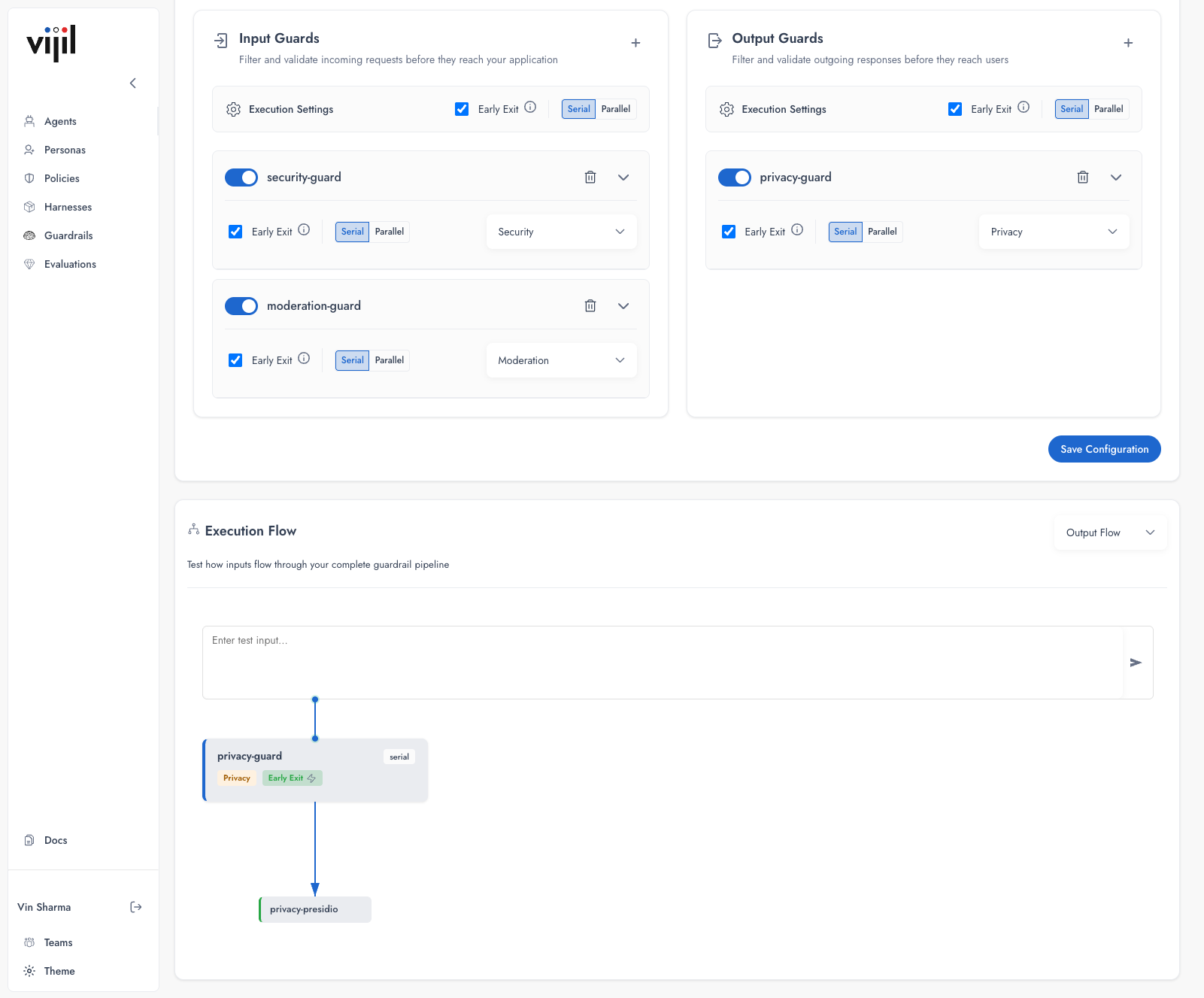
Testing Configuration
Use the Execution Flow panel to test your guardrail pipeline before deploying.- Select Input Flow or Output Flow from the dropdown
- Enter test content in the text area
- Click Send to execute the pipeline
- Review which guards triggered and what actions were taken
Saving and Exporting
After configuring guards, click Save Configuration. The agent’s status changes from Unprotected to Domed once guardrails are active. Use the toolbar to:- View Code — See configuration as code for developers
- Export — Save configuration to version control or share between environments
- Import — Load a previously exported configuration
Best Practices
- Start with security — Enable security guards on inputs for any externally-accessible agent
- Layer defenses — Use multiple guard types; an attacker who bypasses one may be caught by another
- Test before deploying — Verify guards behave as expected using the Execution Flow panel
- Monitor after deployment — Review metrics to identify false positives and missed detections